Am starting this exercise by going to blueteamlabs.online and selecting the lab named in the title. Am provided with a run-down of a situation:Put your phishing analysis skils to the test by triaging and collecting information about a recent phishing campaign. They provide an .eml file which I have to investigate in order to answer the questions presented.
- First step is to download the file which is zip compressed so I open the CLI and change directories to Downloads, ls to show files and then unzip the file I need, next I do cat file_name to see its contents and part of the actual file is the following:
$ cat Your_Account_has_been_locked.eml
Received: from AM7PR06MB6609.eurprd06.prod.outlook.com (2603:10a6:20b:1a6::8)
by AM6PR06MB5954.eurprd06.prod.outlook.com with HTTPS; Tue, 13 Jul 2021
19:14:58 +0000
Received: from BN9PR03CA0911.namprd03.prod.outlook.com (2603:10b6:408:107::16)
by AM7PR06MB6609.eurprd06.prod.outlook.com (2603:10a6:20b:1a6::8) with
Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.4308.22; Tue, 13 Jul
2021 19:14:58 +0000
Received: from BN1NAM02FT027.eop-nam02.prod.protection.outlook.com
(2603:10b6:408:107:cafe::c4) by BN9PR03CA0911.outlook.office365.com
(2603:10b6:408:107::16) with Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.4308.21 via Frontend
Transport; Tue, 13 Jul 2021 19:14:57 +0000
Authentication-Results: spf=pass (sender IP is 45.156.23.138)
smtp.mailfrom=zyevantoby.cn; outlook.com; dkim=pass (signature was verified)
header.d=zyevantoby.cn;outlook.com; dmarc=pass action=none
header.from=zyevantoby.cn;compauth=pass reason=100
Received-SPF: Pass (protection.outlook.com: domain of zyevantoby.cn designates
45.156.23.138 as permitted sender) receiver=protection.outlook.com;
client-ip=45.156.23.138; helo=mta0.zyevantoby.cn;
Received: from mta0.zyevantoby.cn (45.156.23.138) by
BN1NAM02FT027.mail.protection.outlook.com (10.13.2.141) with Microsoft SMTP
Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id
15.20.4308.20 via Frontend Transport; Tue, 13 Jul 2021 19:14:57 +0000
X-IncomingTopHeaderMarker:
OriginalChecksum:6DAD23FF4219F808D7777E2B580FA2F4E342FB9E646D91B86B6224B9813205F6;UpperCasedChecksum:38741B159EC455119696164023D30A92793199076F718A1FBC54B8D472931820;SizeAsReceived:732;Count:8
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; s=default; d=zyevantoby.cn;
h=From:To:Subject:Date:Message-ID:MIME-Version:Content-Type;
i=amazon@zyevantoby.cn;
bh=XikwQS1UwJN7e8YVlXjAYcvssetwLLV4NLN/yq1Tm24=;
b=He0netKWqUJ1/lXLUYmfK9GqNJYVNQpQj1YOimVzuh/BbhGU+INKV9A8EgoVVNIDLdWzCLOybqSS
boFD/zUHOcuNk3zHG9b/OBsMD2LzejOdOfzxx+gxHV3xPqOoTH1atn3pRzeuYfmSS7c+R2Z/qtXD
LV5UggENwZFcL2HoDaA=
From: Amazn amazon@zyevantoby.cn
To: saintington73 saintington73@outlook.com
Subject: Your Account has been locked
Date: Wed, 14 Jul 2021 01:40:32 +0900
Message-ID: <000756bf516d$9bad2034$6e61f7fb$@vinuqou>
Content-Type: multipart/alternative;
boundary=”—-=_NextPart_000_0232_018D8931.1E363E20″
X-IncomingHeaderCount: 8
Return-Path: amazon@zyevantoby.cn
X-MS-Exchange-Organization-ExpirationStartTime: 13 Jul 2021 19:14:57.8225
(UTC)
X-MS-Exchange-Organization-ExpirationStartTimeReason: OriginalSubmit
X-MS-Exchange-Organization-ExpirationInterval: 1:00:00:00.0000000
X-MS-Exchange-Organization-ExpirationIntervalReason: OriginalSubmit
X-MS-Exchange-Organization-Network-Message-Id:
70072381-ba6e-49d1-d12d-08d94632811e
X-EOPAttributedMessage: 0
X-EOPTenantAttributedMessage: 84df9e7f-e9f6-40af-b435-aaaaaaaaaaaa:0
X-MS-Exchange-Organization-MessageDirectionality: Incoming
X-MS-PublicTrafficType: Email
X-MS-Exchange-Organization-AuthSource:
BN1NAM02FT027.eop-nam02.prod.protection.outlook.com
X-MS-Exchange-Organization-AuthAs: Anonymous
X-MS-UserLastLogonTime: 7/13/2021 5:29:27 PM
X-MS-Office365-Filtering-Correlation-Id: 70072381-ba6e-49d1-d12d-08d94632811e
X-MS-TrafficTypeDiagnostic: AM7PR06MB6609:
X-MS-Exchange-EOPDirect: true
X-Sender-IP: 45.156.23.138
X-SID-PRA: AMAZON@ZYEVANTOBY.CN
X-SID-Result: PASS
X-MS-Exchange-Organization-PCL: 2
X-MS-Exchange-AtpMessageProperties: SA|SL
X-MS-Exchange-Organization-SCL: 0
X-Microsoft-Antispam: BCL:0;
X-MS-Exchange-CrossTenant-OriginalArrivalTime: 13 Jul 2021 19:14:57.3917
(UTC)
X-MS-Exchange-CrossTenant-Network-Message-Id: 70072381-ba6e-49d1-d12d-08d94632811e
X-MS-Exchange-CrossTenant-Id: 84df9e7f-e9f6-40af-b435-aaaaaaaaaaaa
X-MS-Exchange-CrossTenant-AuthSource:
BN1NAM02FT027.eop-nam02.prod.protection.outlook.com
X-MS-Exchange-CrossTenant-AuthAs: Anonymous
X-MS-Exchange-CrossTenant-FromEntityHeader: Internet
X-MS-Exchange-CrossTenant-RMS-PersistedConsumerOrg:
00000000-0000-0000-0000-000000000000
X-MS-Exchange-Transport-CrossTenantHeadersStamped: AM7PR06MB6609
X-MS-Exchange-Transport-EndToEndLatency: 00:00:01.3845679
X-MS-Exchange-Processed-By-BccFoldering: 15.20.4308.027
X-Microsoft-Antispam-Mailbox-Delivery:
abwl:0;wl:0;pcwl:0;kl:0;iwl:0;dwl:0;dkl:0;rwl:0;ucf:0;jmr:0;ex:0;auth:1;dest:J;OFR:SpamFilterAuthJ;ENG:(5062000282)(90000117)(90005022)(91005020)(91035115)(91045095)(9050020)(9100314)(5061607266)(5061608174)(4900115)(2008001114)(2008000189)(2102111067)(58390106)(98390106)(8390246)(8377080)(8403011)(8391040)(210498285)(210499095)(210410095)(4920090)(6382023)(4950131)(4990090)(9140004);RF:JunkEmail;
X-Message-Info:
qoGN4b5S4yq3feqfrhbVT4ZV/Ls7bU+S+WMPhEYb5aZT4E8XDAjtC/p3UOvCFKISpmSbFODIS7P1Czbrit2ej0gnU7N5BGvkRYLByvASX+MkLFTto1afNmUaat0b/Bgk9RQNNXEQzWNwvqhmILEi6jAVmjsGSWEt6bAHO28bFLHT7za83r1JmBNHWj8Z0ouj4Dw5mQ0CRkGftM67lE7gXA==
X-Message-Delivery: Vj0xLjE7dXM9MDtsPTA7YT0wO0Q9MjtHRD0yO1NDTD02
X-Microsoft-Antispam-Message-Info:
=?utf-8?B?VGR5SWNzK2xCcDFWUmJwZjkxNy9BcU1rVTRGcTh0b2wzaVlJWUFTdHBILzhK?=
=?utf-8?B?NGJUU0hNTm15S2szeTFLbjh6VTJyU0FiQUZYazNwRUYycFhvRUMvQTU3TkNK?=
MIME-Version: 1.0
——=_NextPart_000_0232_018D8931.1E363E20
Content-Type: text/plain;
charset=”utf-8″
Content-Transfer-Encoding: base64
ICAgICAgICAgICAgICAgICAgICAgICAgIA0KICAgIA0KSGVsbG8gRGVhciBDdXN0b21lciwNCg0K
WW91ciBhz7LPsm91bnQgYWNjZXNzIGhhcyBiZWVuIGxpbWl0ZWQuIFdlJ3ZlIG5vdGljZWQgc2ln
bmlmaWNhbnQgY2hhbmdlcyBpbiB5b3VyIGHPss+yb3VudCBhY3Rpdml0eS4gQXMgeW91ciBwYXlt
ZW50IHByb2Nlc3MsIFdlIG5lZWQgdG8gdW5kZXJzdGFuZCB0aGVzZSBjaGFuZ2VzIGJldHRlcg0K
DQpUaGlzIExpbWl0YXRpb24gd2lsbCBhZmZlY3QgeW91ciBhYmlsaXR5IHRvOg0KzqFheS5DaGFu
Z2UgeW91ciBwYXltZW50IG1ldGhvZC5CdXkgb3IgcmVkZWVtIGdpZnQgY2FyZHMuQ2xvc2UgeW91
ciBhz7LPsm91bnQuDQpXaGF0IHRvIGRvIG5leHQ6DQoNClBsZWFzZSBjbGljayB0aGUgbGluayBh
Ym92ZSBhbmQgZm9sbG93IHRoZSBzdGVwcyBpbiBvcmRlciB0byBSZXZpZXcgVGhlIEFjY291bnQs
IElmIHdlIGRvbid0IHJlY2VpdmUgdGhlIGluZm9ybWF0aW9uIHdpdGhpbiA3MiBob3VycywgWW91
ciBhz7LPsm91bnQgYc+yz7Jlc3MgbWF5IGJlIGxvc3QuDQoNCg0KICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgIA0KDQoNCg0KDQoNCg0KDQoNCg0KDQoNClJldmlldyBBY2NvdW50
DQoNCg0KWW91cnMgU2luY2VyZWx5LCANCg0KQW1hem9uIFN1cHBvcnQgVGVhbQ0KQ29weXJpZ2h0
IMKpIDE5OTktMjAyMSBBbWF6b24uIEFsbCByaWdodHMgcmVzZXJ2ZWQuDQoNCg0KICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICANCg0KDQoNCg0KDQogDQo=
——=_NextPart_000_0232_018D8931.1E363E20
Content-Type: text/html;
charset=”utf-8″
Content-Transfer-Encoding: base64
——=_NextPart_000_0232_018D8931.1E363E20–
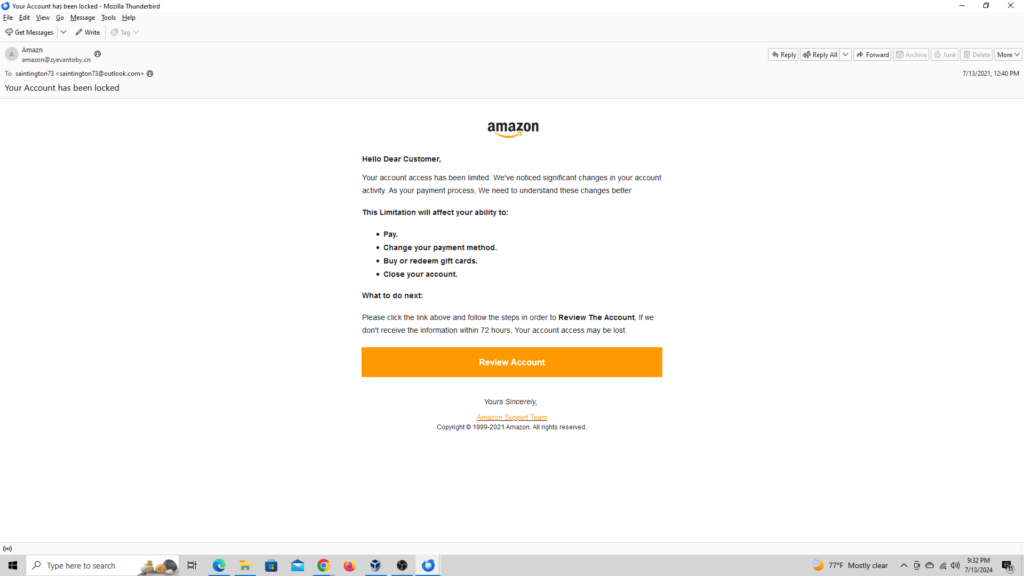
After I went on and opened the file on Mozilla Thunderbird.
Challenge Submissions
1- What is the sending email address?
amazon@zyevantoby.cn
2- What is the recipient email address?
saintington73@outlook.com
3- What is the subject line of the email?
Your Account has been locked
4- What company is the attacker trying to imitate?
Amazon
5- What is the date and time the email was sent? (As copied from a text editor)
Wed, 14 Jul 2021 01:40:32 +0900
6- What is the URL of the main call-to-action button?
With the email open within a safe enviroment in Mozilla Thunderbird I hovered over the Review Account button and copied the redirect URL: https://emea01.safelinks.protection.outlook.com/?url=https%3A%2F%2Famaozn.zzyuchengzhika.cn%2F%3Fmailtoken%3Dsaintington73%40outlook.com&data=04%7C01%7C%7C70072381ba6e49d1d12d08d94632811e%7C84df9e7fe9f640afb435aaaaaaaaaaaa%7C1%7C0%7C637618004988892053%7CUnknown%7CTWFpbGZsb3d8e…
7- Look at the URL using URL2PNG. What is the first sentence (heading) displayed on this site? (regardless of whether you think the site is malicious or not)
For this I google URL2PNG and clicked a website that allowed me to actually see the redirect-to page and pulled the sentence: This web Page Could not be Loaded
8- When looking at the main body content in a text editor, what encoding scheme is being used?
For this one I actually struggled a lot since it clearly says utf-8 in the text editor of the page’s html code, but in the file Your_Account_Has_been-Locked.eml I was able to find the correct Encoding Scheme Base64
9- What is the URL used to retrieve the company’s logo in the email?
Also by inspecting the email saved as HTML and later on opened in a browser, and going to the inspection tab under sources I found a redirect URL for the Amazon logo displayed in the email.(Actual URL modified to avoid troubles)
https://images.confidential-com/content/52e2b6d3ed/1500584238342-OX2L298XVSKF8AO6I3SV/amazon-logo?format=750w&content-type=image%2Fpng
10- For some unknown reason one of the URLs contains a Facebook profile URL. What is the username (not necessarily the display name) of this account, based on the URL?
This one was easy to find by hovering over Amazon Support Team and following the URL straight to the page of (Someone LOL)
